Replace LetsEncrypt SSL with CloudFlare SSL for your Ghost Publication
LetsEncrypt is a great source of Free SSL certificate. But when you use CloudFlare to host your DNS, there are some problems we are facing while issuing the SSL.

Been working with ghost publication for many years & faced some issue often while issuing Letsencrypt SSL.
The main Issue, Letsencrypt cant authenticate your domain when the WWW or A record is Proxied. So you have to turn the Entry record to DNS only from Proxied. & then you can issue a Certificate.
Another issue is LE SSL renews every 90 days. & If you are using proxied option on your DNS record then LE fails to renew the Certificate.
So the Better option to use Cloudflare Generated SSL for your Ghost Publication if you use Cloudflare as your DNS provider. To replace LE SSL with CloudFlare SSL follow the steps below
Create CloudFlare SSL
Login to CloudFlare Account, then go to the SSL Tab > Origin Server > Click Create Certificate
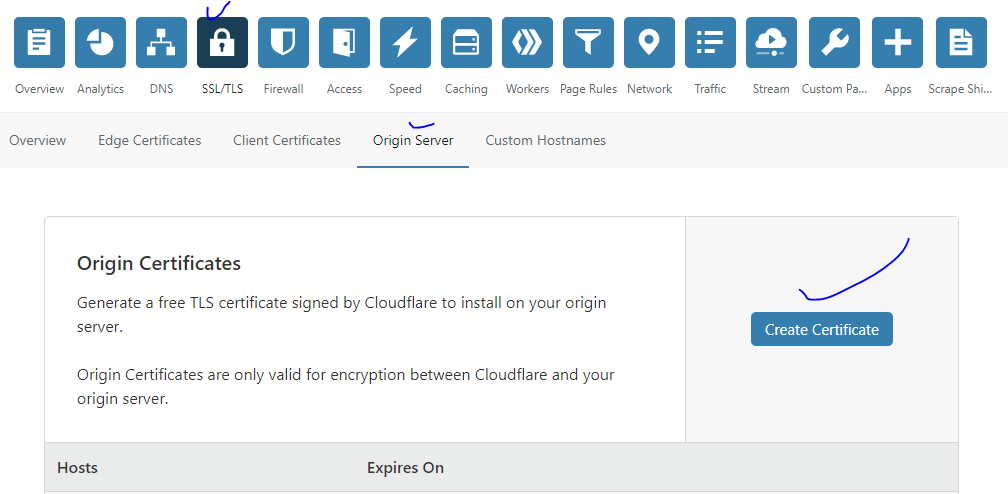
On the next screen keep the setting default & then press Next
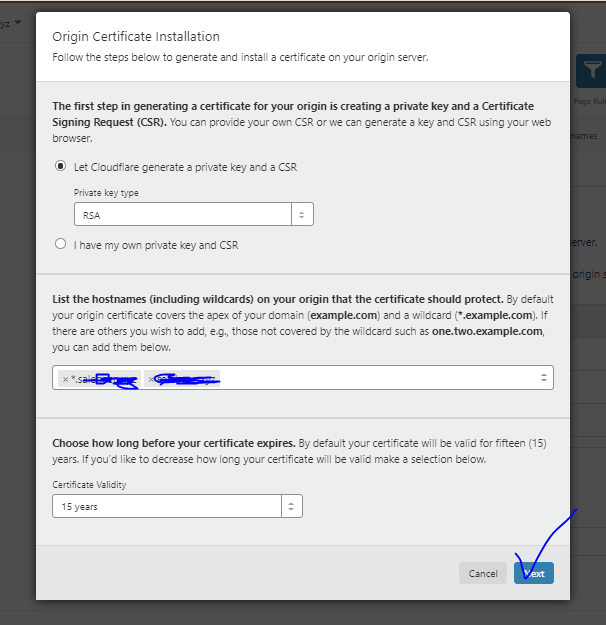
SSL is Created & on next screen you will see the Certificate & Private Key.
Copy the Certificate & save it to your computer as yourdomain.com.crt & also copy the Key & save it as yourdomain.com.key
& the Hit OK
So the first part is done..
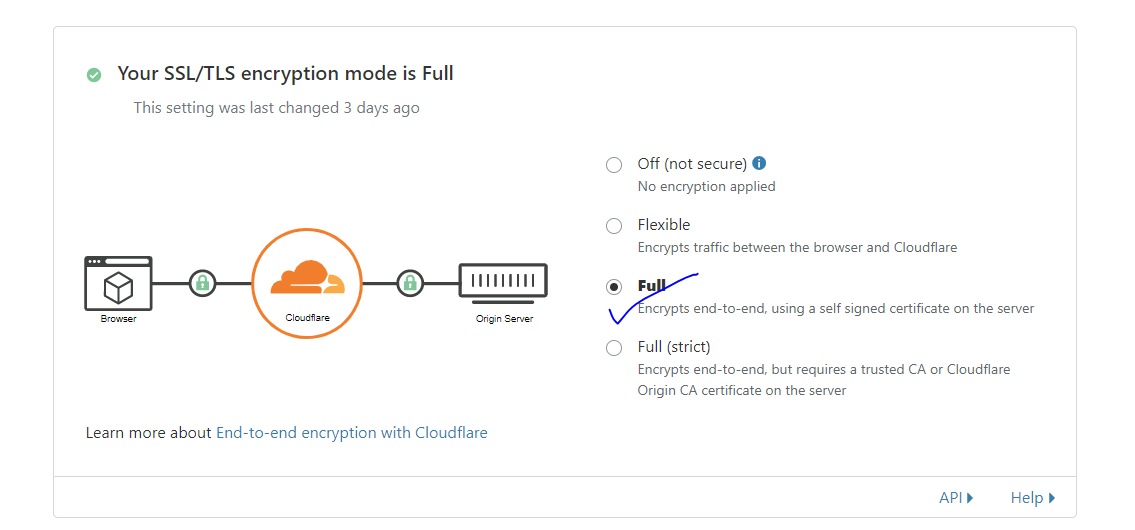
Now go to SSL > Overview & Check the Mode to Full
Add the certificate to your server
Now its time to upload the certificate to your server & configure nginx to use CloudFlare SSL.
Login in to your server via SSH
ssh user@yourserveripCreate a folder under /etc/ssl/
sudo mkdir /etc/ssl/yourdomain.com& upload the Certificate & Private key to that folder you just created
Configuring your ghost publication NGINX Server Block
Lets find you existing Nginx config file for your Ghost Publication first. It should be under following directory & named something like www.yourdomain.com.conf
/etc/nginx/sites-available/www.yourdomain.com.conf& the configuration should be like below
server {
server_name yourdomain.com www.yourdomain.com;
root /var/www/ghost/system/nginx-root; # Used for acme.sh SSL verification (https://acme.sh)
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_pass http://127.0.0.1:2368;
}
location ~ /.well-known {
allow all;
}
client_max_body_size 50m;
listen [::]:443 ssl; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/yourdomain.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/yourdomain.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = yourdomain.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
listen [::]:80;
server_name yourdomain.com;
return 404; # managed by Certbot
}
Now replace your Existing config with the following configuration
server {
listen 80;
listen [::]:80;
server_name yourdomain.com www.yourdomain.com;
location / { return 301 https://$host$request_uri; }
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name yourdomain.com www.yourdomain.com;
ssl_protocols TLSv1.2;
ssl_ciphers HIGH:!MEDIUM:!LOW:!aNULL:!NULL:!SHA;
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:10m;
ssl_certificate /etc/ssl/yourdomain.com/yourdomain.com.crt;
ssl_certificate_key /etc/ssl/yourdomain.com/yourdomain.com.key;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
proxy_pass http://127.0.0.1:2368;
}
client_max_body_size 100M;
}
Save the file & test nginx config
sudo nginx -tAfter the nginx configuration test successfull restart nginx
sudo systemctl restart nginx& you are done.
You ghost publication now will serve via CloudFlare SSL & you don't need to worry about the renewal of the certificate.
Thanks for reading. If you need any help reach out to me via twitter @saleheenkhan1 I will be happy to help